To avoid being victimized by phishing sites, we usually advise examining the address bar for HTTPS presence, avoiding domains with questionable characters like g00gle.com, and discouraging clicking on any recurring or suspicious pop-ups. But what if someone discovered a method to phish passwords without including these characteristics?
One researcher devised a method to completely spoof an OAuth page. It's called a BitB, short for "browser in the browser," which uses a fake browser window within a genuine browser window to mimic an OAuth page. Thousands of websites utilize the OAuth protocol to enable users to log in using their existing accounts with companies like Google, Apple, and Facebook. Instead of having to create an account on the new site, visitors can use an account that they already have—and the magic of OAuth does the rest.
Exploiting User Trust
The photo editing site Canva, for instance, gives visitors the option to login using popular account platforms like Google and Facebook. When accessing the account, after clicking the "sign in" button, a new browser window appears over the top of the existing Canva window.
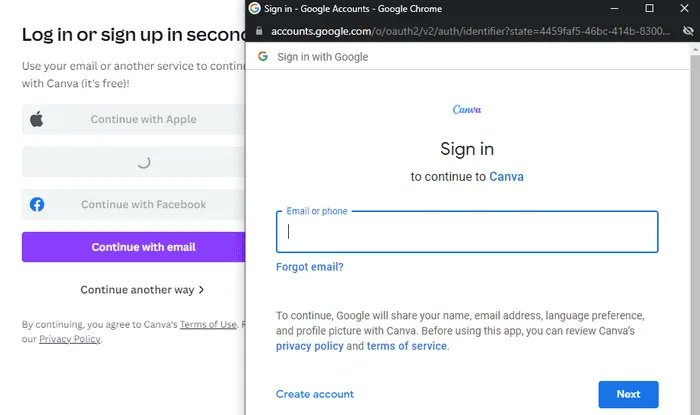
The OAuth procedure guarantees that only Google has access to the user's password. Canva never sees the login information. Instead, OAuth establishes a login session with Google and, when the username and password check out, Google provides the user with a token that allows access to Canva. (Services like PayPal work in a similar manner.)
The BitB approach takes advantage of this method. Instead of creating a genuine second browser window that is linked to the site enabling logins or payments, BitB employs a number of HTML and cascading style sheet (CSS) methods to convincingly impersonate the second window. The fake website has a valid address, complete with a padlock and HTTPS prefix. The window's appearance and operation are identical to the genuine thing. However, it is deployed and strategically designed to exploit the user's privacy.
Last week, a researcher using the handle "mr.d0x" revealed the method. His proof-of-concept attack begins with a web page that accurately imitates Canva. When a visitor logs in using their Apple, Google, or Facebook credentials, a phony Canva page opens a new web page that appears to be the same as the genuine OAuth site.
This new page is also a spoof, with all of the visuals that come the standard Google login. The page also includes the proper Google website address in the address bar. The new window works similarly to a browser window when connected to a genuine Google OAuth session.
If a potential victim opens the fake Canva.com page and tries to login with Google, “it will open a new browser window and go to [what appears to be] the URL accounts.google.com,” mr.d0x wrote. In actuality, the fake Canva site “doesn’t open a new browser window. It makes it LOOK like a new browser window was opened but it’s only HTML/CSS. Now that fake window sets the URL to accounts.google.com, but that's an illusion.”
Know The Signs
The BitB approach is straightforward and effective enough that it's surprising no one has heard of it before. After mr.d0x published about the technique, a few fellow researchers stated how easy it would be for even more seasoned Web users to fall for the ruse.

“This browser-in-the-browser attack is perfect for phishing,” one developer wrote. “If you're involved in malvertising, please don't read this. We don't want to give you ideas.”
This method has previously been employed. In 2020, Zscaler observed a BitB attack used in order to gain access credentials for the popular video game distribution platform, Steam.
The technique, on the other hand, has a few flaws that should offer savvy visitors a foolproof method to determine if something is wrong. Genuine OAuth or payment windows are individual browser instances that are distinct from the primary window. That implies they may be dragged anywhere, including onto the main window's address bar.
The phony websites don't cover the main browser window's address bar, because they're not a separate browser instance. Instead, they're created by custom HTML and CSS and housed within the primary window, which means they can't be covered by fake pages from an alternative program.
Two-factor authentication should be used by everyone who uses Google, Apple, or Facebook. More experienced users can also use the right-click menu on the popup page to "inspect." The URL of a BitB spawn will be hardcoded into the HTML if it is a window created by BitB.
It wouldn't be unusual to discover that the BitB approach has been more widely used, yet mr.d0x's responses demonstrate that even many security defenders are unaware of it, implying that a large number of end users aren't aware of it, either.
You can read more from ARS Technica here.
SeedSpark is a trusted technology resource for small- and medium-sized businesses. From laptop provisioning to new accessories, we’re helping teams connect and communicate with other teams across the country each day. Complete the form and contact our team for a free 30-minute technology assessment. We’ll take time to learn more about your existing technology, assess the situation, and identify new opportunities for improvement that can help you make the most of your technology.



